JVNDB-XXXX-XXXXXX (JVN iPedia Vulnerability ID)
Title
JVN iPedia Vulnerability ID is a unique identifier for each vulnerability stored in JVN iPedia. For example, a number like JVNDB-2007-001234 is assaigned to each vulnerability, where the four-digit number "2007" indicates the year the vulnerability was found and the six-digit number "001234" is an assigned serial number by that year.
"Title" shows what kind of vulnerability exists in what product.
Overview
This section gives a summary of the vulnerability. For more detailed and up-to-date informaton for the vulnerability, please refer to the 'Vendor Information' or 'References' section.
CVSS Severity
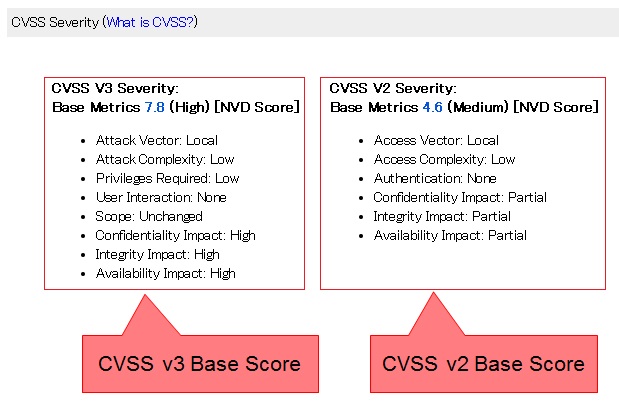
1. What is CVSS?
JVN iPedia uses CVSS (Common Vulnerability Scoring System) and provides a CVSS Base Score along with the metric values used to calculate the score to indicate the severity of each vulnerability. Currently, two versions - CVSS v2 released on June 20, 2007 and CVSS v3 released on June 10, 2015 - coexist. JVN iPedia has begun providing a CVSS v3 score, in addition to a traditional CVSS v2 score, for the vulnerabilities reported through the Information Security Early Warning Partnership since December 1, 2015.
CVSSv2
- "Transition to the New Version of Vulnerability Severity Scoring System CVSS v2" (IPA)(Japanese)
- "CVSS v2 Overview" (IPA)(Japanese)
- "A Complete Guide to the Common Vulnerability Scoring System Version 2.0" (FIRST)
CVSSv3
2. Difference Between CVSS v2 and CVSS v3
CVSS v2 evaluates the severity of vulnerability on a vulnerable host or system. Due to the technological developments, such as the prevalence of virtualization and sandboxing, CVSS v3 has adopted the concept of "component" (vulnerable component and impacted component) and "scope" (whether the impact of the vulnerability is contained within the vulnerable component or goes beyond that) to better evaluate the severity. In addition, in CVSS v3, the Base metrics are further subdivided and the approach to evaluate the Environmental metrics is reviewed to better reflect the real-world implementation.
3. [IPA Score] and [NVD Score]
The note next to a Base Score, IPA Score or NVD Score, indicates who has evaluated the score (see below). When there are both the IPA Score and NVD Score, the IPA Score is shown.
| Indicator | Description |
|---|---|
| [IPA Score] | Shows it is a CVSS Base Score assessed by Information-Technology Promotion Agency (IPA). |
| [NVD Score] | Shows it is a CVSS Base Score used in NVD (National Vulnerability Database) operated by NIST (National Institute of Standards and Technology). |
4. CVSS Calculator
When a CVSS Severity is provided, you can use the CVSS Calculator that enables to calculate a CVSS Severity based on the thee CVSS metrics (Base metrics, Temporal metrics and Environmental metrics). To see how to use the CVSS Calculator, please go here.
Affected Products
This section lists the name and software version of the products (e.g. operating systems, applications, libraries and embedded systems) affected by the vulnerability by vendor name. The product data entered in the search engine are compared with these names.
Impact
This section describes what could happen if the vulnerability is exploited. If there are preconditions required for the attack, such as the administrator privileses, they are also discussed here.
Solution
This section provides the information whethere there are official countermeasures announced by the product vendors. Other related information, such as that on the fixed version and workarounds, is also provided here.
Vendor Information
This section provides the links to each affected vendor's advisories and/or announcements that offer countermeasures, the information on the fixed version and other related information.
If vendor response is not yet available, the link may just point to the vendor's web site.
References
This section provides the links to other resources, such as those offered by JVN, other security organizations and security portals.
Revision History
This section lists the page updates. Minor updates, such as adding some links to 'Vendor Information' or 'References', may not be recorded.
Dates
1. Date Public
It indicates when a given vulnerability became public knowlesge, such as when the vendor issued the advisory, security organizations or security portals published the information or the finder reported it to the public.
2. Date First Published
It indicates when the information on a given vulnerability was published on JVN iPedia.
3. Date Last Updated
It indicates whan the information on a given vulnerability in JVN iPedia was last updated. If no update has been made, Date First Published is shown.
For more information on CVSS, please see here.
Steps
- Click a CVSS v2 or CVSS v3 Base Score in a vulnerability information page in a vulnerability information page. CVSS Caliculator pops up in a new window.
- The CVSS Severity score and its metrics of the vulnerability are passed as the parameters and set to CVSS Calculator.
- Set the CVSS Temporal Score metrics and the CVSS Enviromental Score metrics from the pulldown menus based on information known to you, such as the environment for the usage of the product and attack codes.
1. Basic Search
- Enter what you are looking for in the "Keyword Search" form and click "Search".
- The search results are shown.
- Click an ID number to see the detail of the selected vulnerability.
- Sort the search results accordingly.
- To narrow your search, use Advanced Search.
The initial search results are orderd by ID in descending order (bigger number to smaller number).
The
 or
or  mark next to a column title (e.g. ID, Title) indicates the current sort key and order.
mark next to a column title (e.g. ID, Title) indicates the current sort key and order.
The
 and
and  for each column title mean the following:
for each column title mean the following:
Column Title Sort Order ID Descending (bigger to smaller)
Ascending (smaller to bigger)
Title Descending (bigger to smaller, Z to A)
Ascending (smaller to bigger, A to Z)
CVSSv3 Higer to Lower
Lower to Higher
CVSSv2 Higer to Lower
Lower to Higher
Date Public More Recent to Older
Older to More Recent
Date Last Updated More Recent to Older
Older to More Recent
2. Keyword Search Examples
You could specify things like product names, IDs and attack methods as keywords. A search by more than one keyword (put a space between the keywords) or the partial match search are also available.
Search by Keywords:
- Vendor names (e.g. "Sun", "Fujitsu")
- Product names (e.g. "Apache", "Oracle Database", "Firefox")
- Attack methods (e.g. "cross-site scripting", "buffer overflow", "DoS")
You can use following prefixes for keyword search.- vendor : partial match with vendor names
- product : partial match with product names
Example:
If you specify "vendor:adobe" as a keyword, you can search "adobe" from vendor names.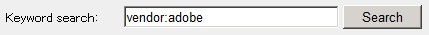
Search by Vendor Advisory IDs:
- Red Hat Security Advisory (e.g. "RHSA-2004:120")
- Turbolinux Security Advisory (e.g. "TLSA-2007-13")
- Turbolinux Security Advisory issued in 2006 ("TLSA-2006")
Search by JVN ID
- VN-JP (e.g. "JVN#47272891", "JVN#")
Search by IDs issued by other security organizations or security portals:
- CVE, NVD (e.g. "CVE-2007-0001")
- US-CERT (e.g. "VU#794752", "TA07-047A", "TA06")
- Xforce (e.g. "27849")
- Secunia (e.g. "SA24109")
3. Advanced Search
Advanced Search provides the following seach parameters. Use multiple criteria and you could narrow down your search.
| Search Parameter | Examples | ||||||||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Keywords | Please refer to 'How to Use Search Engine (Keyword Search Examples)'. | ||||||||||||||||||||
| With Synonym | Searches can be conducted utilizing the synonym dictionary registered on the database. By inserting a "check" in the checkbox, the search results for the keywords as well as the synonyms related to the keywords are returned. | ||||||||||||||||||||
| Vendor | You can specify any vendors registered in JVN iPedia. Select a vendor from the pulldown menu. | ||||||||||||||||||||
| Product | To select a product, first you need to specify a vendor of the product. e.g. Search the information on "Microsoft Windows XP"
|
||||||||||||||||||||
| Vendor / Product search | You can use keyword search to select a product. Click "Vendor / Produc search" button and search by keywords. Example: 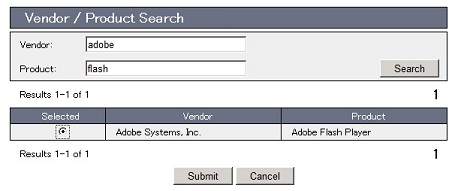 |
||||||||||||||||||||
| Date Public | ou can serch by the date range during which the vulnerabilities have been found. Select the range (year and month) from the pulldown menus. Specifying either the start year/month or the end year/month will work as well. e.g. Search the vulnerabilities found in 2006.
|
||||||||||||||||||||
| Date Last Updated | You can search by the date range during which the vulnerability information has been last updated. Select the range (year and month) from the pulldown menus just like Date Public. | ||||||||||||||||||||
| CVSS Severity | You can search by severity based on CVSS v3 Base Score or CVSS v2 Base Score assigned to each vulnerability. Select the severity level with the check box.For more information on CVSS, please see here.
|
4. Narrow Your Search
After you get the initial hits, you can narrow down your search by the vendor, the product, the date the vulnerability found (Date Publish), the date the vulnerability/countermeasure information last updated (Date Last Updated) and the CVSS severity using Advanced Search.


