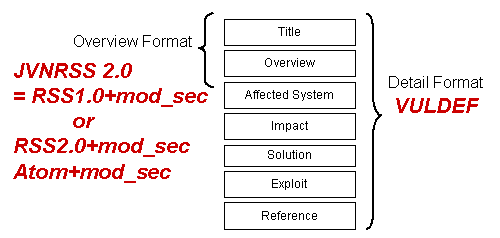
This document provides information for the JVNRSS XML format.
In order to gather the information and perform the relationship between the gathered information, it is necessary to improve the method of the security information sharing. If the security information is machine readable, many Internet sites can reduce the cost of information gathering. Our security information sharing proposes the XML formats as to approach solving these problems. JVNRSS is the overview XML format based on RSS with mod_sec (http://jvndb.jvn.jp/en/schema/mod_sec.html) and VULDEF (http://jvnrss.ise.chuo-u.ac.jp/jtg/vuldef/) is the detail XML format.

The members of JVNRSS Feasibility Study Team:
Comments should be directed to the JVN Working Group.
Copyright © 2003-2009 by the Authors.
Permission to use, copy, modify and distribute the JVNRSS 2.0 Specification and its accompanying documentation for any purpose and without fee is hereby granted in perpetuity, provided that the above copyright notice and this paragraph appear in all copies. The copyright holders make no representation about the suitability of the specification for any purpose. It is provided "as is" without expressed or implied warranty.
This copyright applies to the JVNRSS 2.0 Specification and accompanying documentation and does not extend to the JVNRSS format itself.
JVNRSS is based on RDF Site Summary (RSS) 1.0 and uses the field <sec:references> of Qualified Security Advisory Reference (mod_sec) as index of grouping security information. JVNRSS with the Relational ID in <sec:references> is shown.
<item rdf:about="URL of security information"> <title>Title</title> <link>URL of security information</link> <dscription>Outline of security information</description> <dc:publisher>Product vendor name</dc:publisher> <dc:creator>Contact point information</dc:creator> <sec:identifier>Security information ID</sec:identifier> <sec:references>Relational ID (1) {CVE|CERT-CA|CERT-VU|etc.}</sec:references> <sec:references>Relational ID (2) {CVE|CERT-CA|CERT-VU|etc.}</sec:references> <sec:references> : : </sec:references> <dc:date>Date last updated</dc:date> <dcterms:issued>Date first published</cterms:issued> <dcterms:modified>Date last updated</dcterms:modified> </item>
JVNRSS contains a list of items, each of which is identified by a link. Each item can have any amount of metadata associated with it. The most basic metadata supported by RSS includes a title for the link and a description of it. And our proposal Relational ID allows the security information on the different sites to relate each other. The URL of major references such as Common Vulnerability Exposure (CVE), CERT Advisory (CERT-CA), CERT Vulnerability Notes (CERT-VU, US-CERT Vulnerability Notes), US-CERT Technical Alert and DOE-CIRC Technical Bulletin are used as Relational ID. These are best reference URL for Internet security information.
http://jvndb.jvn.jp/schema/jvnrss_2.0.xsd
The opening RDF tag assocaties the rdf: namespace prefix with the RDF syntax schema, establishes the RSS 1.0 schema, Dublin Core, Qualified Dublin Core and Qualified Security Advisory Reference (mod_sec) as the default namespace for the document.
Example:
<rdf:RDF
xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"
xmlns:rdf="http://www.w3.org/1999/02/22-rdf-syntax-ns#"
xmlns="http://purl.org/rss/1.0/"
xmlns:dc="http://purl.org/dc/elements/1.1/"
xmlns:dcterms="http://purl.org/dc/terms/"
xmlns:sec="http://jvn.jp/rss/mod_sec/"
xsi:schemaLocation="http://purl.org/rss/1.0/
http://jvndb.jvn.jp/schema/jvnrss_2.0.xsd">
The channel element contains metadata describing the channel of secuiry information itself, including a title, brief description, and URL link to the described resource.
Syntax: <channel rdf:about="{resource (URL of security information channel) }">
Requirement: REQUIRED
Example:
<channel rdf:about="http://jvn.jp/rss/jvn.rdf"> [Required] <title>JVNRSS Feed - Update Entry</title> [Required] <link>http://jvn.jp/</link> [Required] <description>JVN What's New</description> [Required] <dc:publisher>JVNRSS Feasibility Study Team</dc:publisher> [Required] <dc:creator>jvn@jvn.jp</dc:creator> [Required] <dc:right>Copyright © 2006 by the Authors.</dc:right> [Optional] <dc:date>2006-04-03T10:04+09:00</dc:date> [Required] <dcterms:issued /> [Optional] <dcterms:modified>2006-04-03T10:04+09:00</dcterms:modified> [Optional] <items> <rdf:Seq> <rdf:li rdf:resource="http://jvn.jp/cert/JVNVU834865" /> [Required] <rdf:li rdf:resource="http://jvn.jp/cert/JVNTA06-062A" /> [Required] </rdf:Seq> </items> </channel>
A descriptive title for the channel of security information.
Syntax: <title>{channel_title (Title of security information channel) }</title>
Requirement: REQUIRED
The URL to which an HTML rendering of the channel title will link, commonly the parent site's security information page.
Syntax: <link>{channel_link (URL of security information page) }</link>
Requirement: REQUIRED
A brief description of the channel of security information.
Syntax: <description>{channel_description (Outline of security information) }</description>
Requirement: REQUIRED
An organization name (typically product vendor name) responsible for making the security information available.
Syntax: <dc:publisher>{channel_dc:publisher (product vendor name) }</dc:publisher>
Requirement: RECOMMENDED
Information about rights held in and over the security information.
Syntax: <dc:rights>{channel_dc:rights}</dc:rights>
Requirement: OPTIONAL
A Contact point information (email address is recommended) responsible for making the security information available.
Syntax: <dc:creator>{channel_dc:creator (Contact point information) }</dc:creator>
Requirement: RECOMMENDED
This is the date the security information was last updated. This date is also updated when a vendor security information document changes.
Complete date plus hours and minutes: YYYY-MM-DDThh:mmTZD (eg 1997-07-16T19:20+01:00) (See W3CDTF: Date and Time Formats)
Syntax: <dc:date>{channel_dc:date}</dc:date>
Requirement: RECOMMENDED
This is the date when an organization (typically product vendor) first published the security information. This date should be the date public or later.
Complete date plus hours and minutes: YYYY-MM-DDThh:mmTZD (eg 1997-07-16T19:20+01:00) (See W3CDTF: Date and Time Formats)
Syntax: <dcterms:issued>{channel_dcterms:issued}</dcterms:issued>
Requirement: RECOMMENDED
This is the date the security information was last updated. This date is also updated when a vendor security information document changes.
Complete date plus hours and minutes: YYYY-MM-DDThh:mmTZD (eg 1997-07-16T19:20+01:00) (See W3CDTF: Date and Time Formats)
Syntax: <dcterms:modified>{channel_dcterms:modified}</dcterms:modified>
Requirement: RECOMMENDED
An RDF table of contents, associating the document's items [3.3] with this particular JVNRSS channel. Each item's rdf:resource {item_uri} must be the same as the associated item element's rdf:about {item_uri}.
Syntax: <items><rdf:Seq><rdf:li resource="{item_uri}" /> ... </rdf:Seq></items>
Requirement: REQUIRED
A security information headline. {item_uri} must be unique with respect to any other rdf:about attributes in the JVNRSS document and is a URL which identifies the item.
Syntax: <item rdf:about="{item_uri (URL of Product vendor security information) }">
Requirement: REQUIRED
Example:
<item rdf:about="http://jvn.jp/cert/JVNVU834865"> <title>Sendmail contains a race condition</title> <link>http://jvn.jp/cert/JVNVU834865</link> <description>A race condition in Sendmail may allow a remote attacker to execute arbitrary code.</description> <dc:publisher>JVNRSS Feasibility Study Team</dc:publisher> <dc:creator>jvn@jvn.jp</dc:creator> <sec:identifier>JVNVU#834865</sec:identifier> <sec:references>http://www.us-cert.gov/cas/techalerts/TA06-081A.html</sec:references> <sec:references>http://www.kb.cert.org/vuls/id/834865</sec:references> <sec:references>http://cve.mitre.org/cgi-bin/cvename.cgi?name=2006-0058</sec:references> <dc:date>2006-04-03T10:30+09:00</dc:date> <dcterms:issued>2006-03-23T04:00+09:00</dcterms:issued> <dcterms:modified>2006-04-03T10:30+09:00</dcterms:modified> </item>
The item's title for security information.
Syntax: <title>{item_title (Title of Product vendor security information) }</title>
Requirement: REQUIRED
The item's URL for security information.
Syntax: <link>{item_link}</link>
Requirement: REQUIRED
A brief description/abstract of the item for security information.
Syntax: <description>{item_description (Outline of Product vendor security information) }</description>
Requirement: RECOMMENDED
A product vendor name, an organization name , or a site name for the item for security information.
Syntax: <dc:publisher>{Product vendor name}</dc:publisher>
Requirement: RECOMMENDED
An entity primarily responsible for making the content of the resource. Typically, the name of a Creator should be email address for contact.
Syntax: <dc:creator>{Contact point information}</dc:creator>
Requirement: OPTIONAL
A unique identifier assigned by vendor.
Syntax: <sec:identifier>{Security information ID assigned by vendor}</sec:identifier>
Requirement: RECOMMENDED
A best reference URL (CVE, CERT Advisory, CERT Vulnerability Note, US-CERT Technical Alert etc.) to a related security information.
Best reference URLs are followings.
Syntax: <sec:references>{Relational ID}</sec:references>
Requirement: RECOMMENDED
Its value is a date, indicating when the item was last updated.
Complete date plus hours and minutes: YYYY-MM-DDThh:mmTZD (eg 1997-07-16T19:20+01:00) (See W3CDTF: Date and Time Formats)
Syntax: <dc:date>{Date last updated}</dc:date>
Requirement: RECOMMENDED
Its value is a date, indicating when the item was first published.
Complete date plus hours and minutes: YYYY-MM-DDThh:mmTZD (eg 1997-07-16T19:20+01:00) (See W3CDTF: Date and Time Formats)
Syntax: <dcterms:issued>{Date first published}</dcterms:issued>
Requirement: RECOMMENDED
Its value is a date, indicating when the item was last updated.
Complete date plus hours and minutes: YYYY-MM-DDThh:mmTZD (eg 1997-07-16T19:20+01:00) (See W3CDTF: Date and Time Formats)
Syntax: <dcterms:modified>{Date last updated}</dcterms:modified>
Requirement: RECOMMENDED
A JVNRSS 2.0 document, making use of the core RSS 1.0, Dublin Core, Qualified Dublin Core and Qualified Security Advisory Reference (mod_sec) element set.
A basic JVNRSS 2.0 document is based on REQUIRED and RECOMMENDED entries.
<?xml version="1.0" encoding="UTF-8" ?>
<rdf:RDF
xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"
xmlns:rdf="http://www.w3.org/1999/02/22-rdf-syntax-ns#"
xmlns="http://purl.org/rss/1.0/"
xmlns:dc="http://purl.org/dc/elements/1.1/"
xmlns:dcterms="http://purl.org/dc/terms/"
xmlns:sec="http://jvn.jp/rss/mod_sec/"
xsi:schemaLocation="http://purl.org/rss/1.0/
http://jvndb.jvn.jp/schema/jvnrss_2.0.xsd"
xml:lang="en"
>
<channel rdf:about="http://jvn.jp/rss/jvn.rdf">
<title>JVNRSS Feed - Update Entry</title>
<link>http://jvn.jp/</link>
<description>JVN What's New</description>
<dc:publisher>JVNRSS Feasibility Study Team</dc:publisher>
<dc:creator>jvn@jvn.jp</dc:creator>
<dc:date>2006-04-03T10:04+09:00</dc:date>
<dcterms:issued />
<dcterms:modified>2006-04-03T10:04+09:00</dcterms:modified>
<items>
<rdf:Seq>
<rdf:li rdf:resource="http://jvn.jp/cert/JVNVU834865" />
<rdf:li rdf:resource="http://jvn.jp/cert/JVNTA06-062A" />
</rdf:Seq>
</items>
</channel>
<item rdf:about="http://jvn.jp/cert/JVNVU834865">
<title>Sendmail contains a race condition</title>
<link>http://jvn.jp/cert/JVNVU834865</link>
<description>A race condition in Sendmail may allow a remote attacker
to execute arbitrary code.</description>
<dc:publisher>JVNRSS Feasibility Study Team</dc:publisher>
<dc:creator>jvn@jvn.jp</dc:creator>
<sec:identifier>JVNVU#834865</sec:identifier>
<sec:references>http://www.us-cert.gov/cas/techalerts/TA06-081A.html</sec:references>
<sec:references>http://www.kb.cert.org/vuls/id/834865</sec:references>
<sec:references>http://cve.mitre.org/cgi-bin/cvename.cgi?name=2006-0058</sec:references>
<dc:date>2006-04-03T10:30+09:00</dc:date>
<dcterms:issued>2006-03-23T04:00+09:00</dcterms:issued>
<dcterms:modified>2006-04-03T10:30+09:00</dcterms:modified>
</item>
<item rdf:about="http://jvn.jp/cert/JVNTA06-062A">
<title>Apple Mac Products are Affected by Multiple Vulnerabilities</title>
<link>http://jvn.jp/cert/JVNTA06-062A</link>
<description>Apple has released Security Update 2006-001 to correct
multiple vulnerabilities affecting Mac OS X, Mac OS X Server, Safari web browser,
and other products. The most serious of these vulnerabilities may allow a remote
attacker to execute arbitrary code. Impacts of other vulnerabilities include
bypassing security restrictions and denial of service.</description>
<dc:publisher>JVNRSS Feasibility Study Team</dc:publisher>
<dc:creator>jvn@jvn.jp</dc:creator>
<sec:identifier>JVNTA06-062A</sec:identifier>
<sec:references>http://www.us-cert.gov/cas/techalerts/TA06-062A.html</sec:references>
<sec:references>http://cve.mitre.org/cgi-bin/cvename.cgi?name=2006-0848</sec:references>
<sec:references>http://cve.mitre.org/cgi-bin/cvename.cgi?name=2005-4504</sec:references>
<sec:references>http://cve.mitre.org/cgi-bin/cvename.cgi?name=2006-0387</sec:references>
<dc:date>2006-03-15T17:30+09:00</dc:date>
<dcterms:issued>2006-03-06T11:00+09:00</dcterms:issued>
<dcterms:modified>2006-03-15T17:30+09:00</dcterms:modified>
</item>
</rdf:RDF>
A customised example for JVNRSS 2.0 document includes all mod_sec (http://jvndb.jvn.jp/schema/mod_sec_2.0.xsd) entries.
JVNRSS Feasibility Study Team thanks the following for working with us for all their continued discussion and input.